
Long before ChatGPT, movies (and other media) warned us of the dangers of creations outstripping their creators. One basic plot involves machines: Humans want help for their tasks, so they develop machines to help, and all is well at first. The humans then say let’s take it further and they give the machines sophistication in the form of Artificial Intelligence or “AI.” But, according to the familiar pattern, the machines find the humans threatening or figure out that the humans ARE the problem to their own happiness. Thus the machines turn on the humans, literally, and all goes badly for both sides.
In the world of BSA this plot seems to have played out as well. Following the events of 9/11 and other events involving criminal activity in banking, it became clear that more was needed to overcome the lack of sophistication in monitoring customers and their transactional activity for suspicious behavior. This need gave way to the implementation of what BSA calls “Surveillance Monitoring” or Automated Account Monitoring, a form of AI in banking. The idea was that surveillance monitoring could go beyond core systems in identifying potential suspicious activity. Specifically, these systems would analyze identify individual transactions, patterns of unusual activity, or deviations from expected activity. The transactions would typically involve a wide range of account activity, such as deposits, withdrawals, fund transfers, ACH, ATM, wire, etc. and then use a series of rule-based algorithms to draw out what merited attention. In other words, the systems are using AI.
The Power of Computing
It doesn’t take watching many AI take-over movies to know that computers can do things that no human could dream of doing. They can compute massive amounts of data in fractional periods that are rather shocking. Supercomputer Fugaku scored 442.01 PFlop/s in a recent test. What is a PFlop you might ask? Well, a gigaflop is a billion floating-point operations per second. A teraflop is one trillion. A petaflop of PFLOP is a quadrillion floating-point operation per second. That is a lot of computing! One might wonder what good is a human being if a machine could handle that much data.
When automated surveillance systems were launched some 20 years ago, they were seen as powerful allies in the effort to identify activity meriting review. They offered a variety of approaches aimed at detecting behavior on a customer level as well as across transactional patterns. Organizations launched departments with this new “weapon” against financial crime and saw success. Moreover, the expectation by various sides was that the absence of such a system was tantamount to dismissal of best-practices and resulted in heavy criticism or worse.
Suffice it to say that automated surveillance systems have become the expectation rather than the exception. But what have they become over the past twenty years? AdvisX finds more and more organizations that have become dominated by these systems. Rather than the system being one part of the arsenal of the organization, the organization has become dominated by the system. This results in powerful negatives from a human perspective as individuals work to meet the requirements of the system rather than the system meeting the requirements of the regulation. The tool that was supposed to streamline work by identifying at-risk activity or customers is often creating excessive work, with much of it unnecessary.
Alert Fatigue
Imagine if you’re a BSA/AML Analyst and you’re being assigned 100 alerts to review in a given week. Then imagine if 95 of those alerts are pretty much identifying activity that is an outlier but explainable. The problem for many analysts is alert fatigue. Finding the one in 20 alerts that has merit for case escalation is a challenge when you multiple the situation by weeks, months, and years. As a result, analyst burn-out is significant. Moreover, the best analysts are likely to burn out faster, leaving the organization.
It is probably important to remember that while the regulation doesn’t specifically require such a system, it is obvious that such systems are here to stay for even smaller organizations. However, it is important that an organization understands that the automated surveillance system is first and foremost a tool and not the complete solution. Consider the following graphic that, for quite some time, has been part of the FFIEC Examination Manual, regarding key suspicious activity monitoring components:
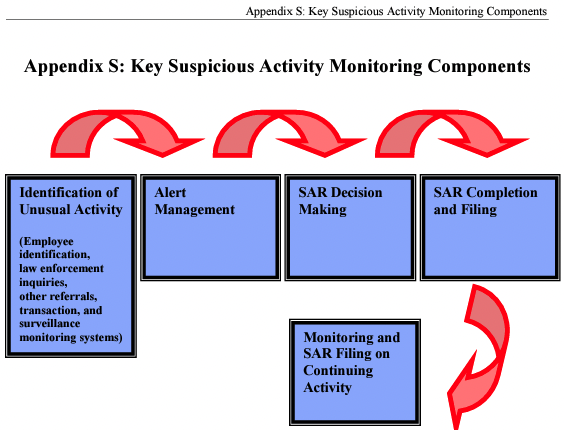
The identification of unusual activity is critical to each organization that is covered by the Bank Secrecy Act/Anti-Money Laundering or BSA/AML. A pattern of priorities shows up as you review the means of identification of suspicious activities. First is the importance of first level of defense, or employees. Second are outside events such as 314(a) or (b) notifications. Transaction and surveillance monitoring systems come third. However, none of these are the ends to the process, but rather a part of the full cycle. Once these sources trigger, the next efforts involve the most important asset of any organization: people.
What Humans Contribute

In terms of synaptic transmissions, the human brain is woefully slow compared to a computer. Like, millions and millions of times slower. But BSA/AML isn’t just raw computing. It is about “knowing.” Computing has certain value or merit but there is so much more than that when it comes to Know Your Customer or KYC. The knowledge of a customer is more than just how much they’ll be depositing monthly or where they’re located. It is about various elements that must be appreciated individually and collectively to understand if the customer relationship and transactional activity “fit” based on the presented information. This is as much art as it is science and the artistic part of what happens in AML is critical.
To further elaborate on the subject of art, let’s discuss the art of physical motion and response in tennis. One article in Nautilus discussed how a pro tennis player can follow the trajectory of a ball served at a speed up to 160 mph and move to the optimal spot on the court, position his or her arm, and swing the racket to return the ball in the opponent’s court, all within a few hundred milliseconds. The amount of power needed to perform these tasks is relatively small and does not happen in serial steps but rather in a cascade of operations.
Computers are largely serial and follow required actions as they’re programmed. The human brain employs massive parallel processing and takes advantage of a large number of neurons and large number of connections each neuron makes. For instance, the moving tennis ball activates many cells in the retina called photoreceptors, whose job is to convert light into electrical signals. These signals are then transmitted to many different kinds of neurons in the retina in parallel. By the time signals originating in the photoreceptor cells have passed through two to three synaptic connections in the retina, information regarding the location, direction, and speed of the ball has been extracted by parallel neuronal circuits and is transmitted in parallel to the brain. Likewise, the motor cortex (the part of the cerebral cortex that is responsible for volitional motor control) sends commands in parallel to control muscle contraction in the legs, the trunk, the arms, and the wrist, such that the body and the arms are simultaneously well positioned to receiving the incoming ball. As of today, humans cannot be rivaled when it comes to tennis. At least in the physical world, and for the foreseeable future, this is likely to remain the case. In the real world, humans are still on top.
BSA/AML is Built on Human Computing Power
If surveillance monitoring systems were everything, then you wouldn’t need a department of analysts. The computers could figure it all out and handle everything from monitoring to detection to reporting. But machines often can’t figure it out. Humans understand beyond what the computer sees. This is why it is critical that training is the highest priority for an organization to ensure that it meets the requirements of BSA/AML. However, the concept goes even further.
Validating that a surveillance monitoring system is “performing” accurately is always important. But what is perhaps more important is that the system is utilized as a tool and not as the end-all-be-all. For example, just because a system generates an alert doesn’t mean that the alert has value. Organizations that fail to impose enhanced understanding of alerts (aka efficiency) will become tethered to those alerts. Using alerts as part of an organization’s approach to BSA/AML requires new thinking. If the organization knows its customers, it knows that system alerts will vary in value based on that knowledge of customers. Often systems will engage in additional consideration to place hierarchical value on alerts. Such effort has value but is often impacted by what information is available within the system. Often, our experience shows us, there is valuable information not considered by the system that would further enhance automated system output or, in other words, effectiveness. By applying those overlays on a system, the organization turbo-charges their approach, minimizing workloads and beginning to use the system as it was designed: a tool in the work chest of an organization.
When an automated surveillance system is truly effective, it acts more of a cross-check against the organization’s knowledge of their customer base. The system generates and the organization evaluates those results against expectations. This predictive analytical process is forward-looking and gives organizations the basis for further reducing workloads by identifying productive use of resources.
The Artistry of BSA/AML

It is possible that a great work of literature could be created by a machine. Nowadays you can use AI to write a pretty decent script. But let’s be honest, the prose of AI, while technically sound, often leaves quite a bit wanting. There is something about the artist that cannot yet be achieved.
Over the 20+ years now of BSA/AML systems, we have seen intelligent systems provide assistance in detecting activities that merit investigation. But those systems, while often useful, cannot replace the artisans of BSA/AML, the personnel of an organization from the 1st line to the 3rd line. They are the keys. But what is happening is a failure to properly use the system as it was intended. The computer can be very effective in achieving a program, but it is not the program itself. AdvisX continues to seek new opportunities to work with organizations to not only validate their “systems” or “models” but to evaluate how those systems/models might take their proper role. Systems and models are tools, and AdvisX can help reduce the workload of that tool without sacrificing its merit. If this is something that you too feel has value for exploring, we invite you to contact us and speak with us. Human to human.


